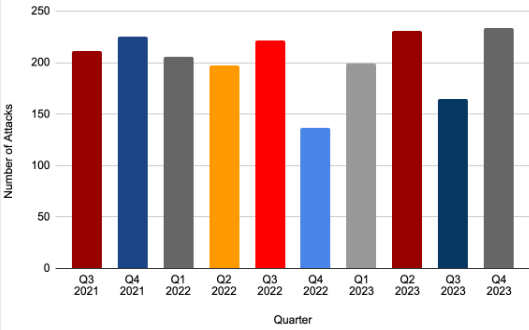
Earlier this year, Mandiant’s Managed Defense threat hunting team identified an UNC2975 malicious advertising (“malvertising”) campaign presented to users in sponsored search engine results and social media posts, consistent with activity reported in From DarkGate to DanaBot. This campaign dates back to at least June 19, 2023, and has abused search engine traffic and leveraged malicious advertisements to affect multiple organizations, which resulted in the delivery of the DANABOT and DARKGATE backdoors.
Managed Defense worked with Advanced Practices and with the Google Anti-Malvertising team to remove the malicious advertisements from the ads ecosystem, and subsequently alerted other impacted organizations to also take actions against this campaign.
This blog post covers the details of recently discovered infrastructure operated by the distribution threat cluster UNC2975, which Mandiant has tracked since 2021, that leveraged malicious advertisements to trick users into visiting fake “unclaimed funds” themed websites. In this UNC2975 campaign, the malicious websites delivered PAPERDROP and PAPERTEAR downloader malware that eventually led to DANABOT and DARKGATE backdoor malware. This blog post also highlights how Mandiant’s findings result in takedowns of malicious ad campaigns served on Google infrastructure.