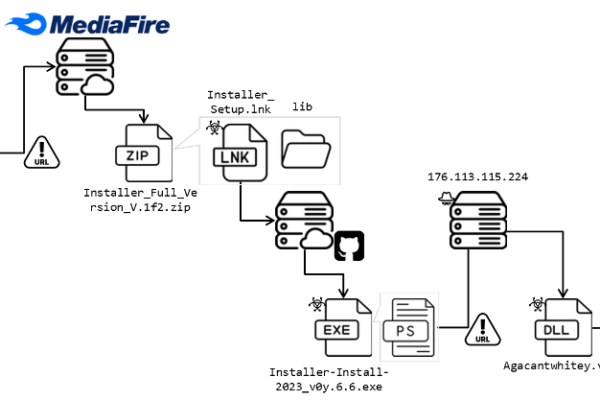
New Go loader pushes Rhadamanthys stealer
READ ARTICLE Posted: March 22, 2024 by Jérôme Segura Malware loaders (also known as droppers or downloaders) are a popular commodity in the criminal underground. Their primary function is to successfully compromise a machine and deploy one or multiple additional payloads. A good loader avoids detection and identifies victims as legitimate (i.e. not sandboxes) before pushing other…