Posted: March 22, 2024 by Jérôme Segura
Malware loaders (also known as droppers or downloaders) are a popular commodity in the criminal underground. Their primary function is to successfully compromise a machine and deploy one or multiple additional payloads.
A good loader avoids detection and identifies victims as legitimate (i.e. not sandboxes) before pushing other malware. This part is quite critical as the value of a loader is directly tied to the satisfaction of its “customers”.
In this blog post, we describe a malvertising campaign with a loader that was new to us. The program is written in the Go language and uses an interesting technique to deploy its follow-up payload, the Rhadamanthys stealer.
Malicious ad targets system administrators
PuTTY is a very popular SSH and Telnet client for Windows that has been used by IT admins for years. The threat actor bought an ad that claims to be the PuTTY homepage and appeared at the top of the Google search results page, right before the official website.
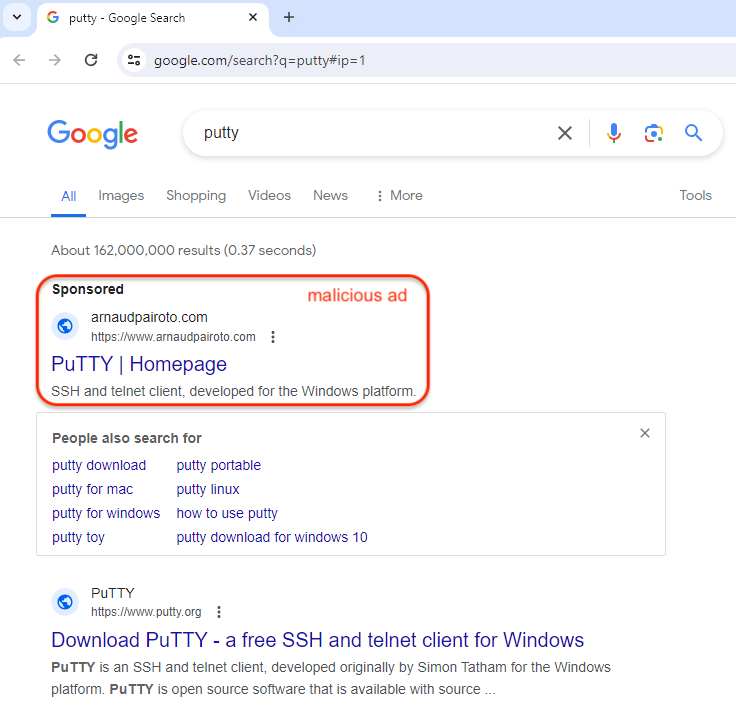
In this example, the ad looks suspicious simply because ad snippet shows a domain name (arnaudpairoto[.]com) that is completely unrelated. This is not always the case, and we continue to see many malicious ads that exactly match the impersonated brand.
Fake PuTTY site
The ad URL points to the attacker controlled domain where they can easily defeat security checks by showing a “legitimate” page to visitors that are not real victims. For example, a crawler, sandbox or scanner, will see this half finished blog:

Real victims coming from the US will be redirected to a fake site instead that looks and feels exactly like putty.org. One of the big differences though is the download link.