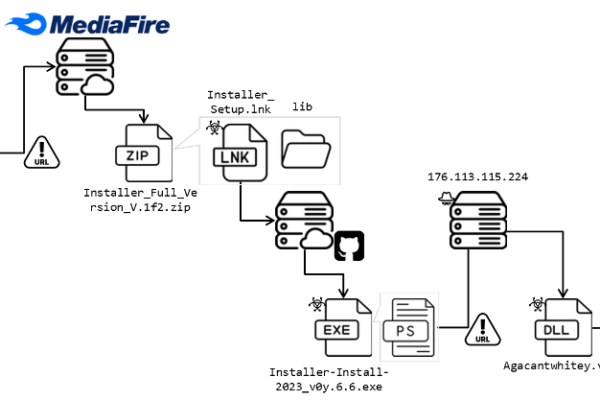
Red Pandas Unleashed: How Webhooks, Bad USB, and WiFi Collide in Cyberspace
Read Article The Power of Automation for Pentesting Automation has become a game-changer in the world of penetration testing. With the ever-increasing complexity of networks and systems, manually tracking and responding to security events is no longer viable. This is where webhooks come into play for cybersecurity professionals, and where we as pentesters can abuse…